Email encryption is a powerful tool organizations can utilize to protect sensitive information. This is especially necessary if email communication has become your primary form of corporate communication. However, the real question is: how much protection does an organization need? This blog post will explain various types of encryption mechanisms an organization can use so that you can figure out the protection method that is best for you.
How Email Currently Works
In today’s world most organizations utilize an internal mail server (i.e. Exchange) and mail client (i.e. Outlook) as their email infrastructure. That being said, how does email currently work in these environments?
In the typical internal mail server/mail client scenario, all email communication by default uses the SMTP plain text protocol to send messages. This means that emails sent/received inside the organization are not encrypted while in transit or at rest (in the user’s mailbox). The same goes for emails sent outside the organization. You can improve security in this environment by enabling the SSL version of SMTP, but keep in mind that while messages with this configuration will encrypt the message in transit (guaranteed just inside the organization), they are not encrypted when they arrive in the user’s mailbox.
Using a Cloud Provider
These days more and more organizations are beginning to use Cloud providers as their email solution. While maintaining your own mail server will give you absolute control of your email, it takes resources to maintain this solution. Using a commercial Cloud provider shifts the burden of hardware/software maintenance, and security to the provider but it comes at the cost of losing control of how your email is maintained, stored, archived, etc.
In a Cloud environment, users can either connect to their email through a typical mail client or through a web browser. Connecting to the Cloud provider’s email through a web browser will almost certainly be through HTTPS, securing the session between your computer and the provider, which is a good start. Connecting to the Cloud provider through a mail client works in similar fashion in that you can choose to connect through an encrypted port vice the default plain text SMTP/POP port.
Specific Encryption Mechanisms
In a general sense this is how email can be configured. What follows below are the specific encryption mechanisms an organization can use, along with a brief explanation, to improve their overall email security posture.
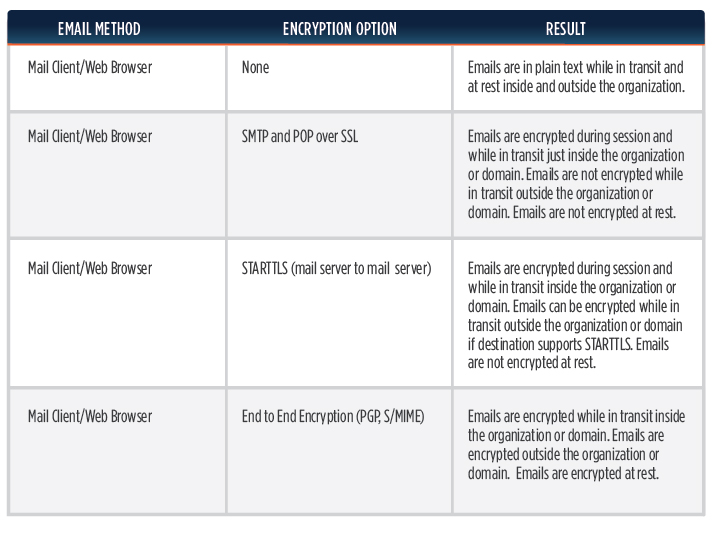
As you can see, the End to End encryption option using PGP or S/MIME offers the strongest protection against email confidentiality and integrity, as the body of the email message can only be read by the intended recipient. Unfortunately, End to End encryption is the most complex to implement in the Enterprise. The Federal Government and some large private organizations implement End to End encryption through the use of Public Key Infrastructure (public/private certs), which in most cases involves the use of a token in addition to passwords.
Another benefit of the PGP & S/MIME option is that it offers the benefit of Digital Signatures. Digitally signing an email ensures that the sender of the email is who they say they are and enforces non-repudiation. As noted, while this solution is the most secure, it is also the most complex.
Another email security option that is catching on is the use of STARTTLS, which is a mail server to mail server encryption protocol. The push/strategy behind this protocol is to eventually influence all mail server providers to use STARTTLS, so that eventually all email communication across any organization or domain can be encrypted while in transit. STARTTLS has some advantages over PGP in that it’s much easier to implement and STARTTLS actually encrypts email metadata, something that PGP does not do. Google, Facebook, Verizon, Comcast and others already support the STARTTLS protocol and the list continues to grow. You can check out Google’s encryption transparency report for more information about who supports STARTTLS:
https://www.google.com/transparencyreport/saferemail/
Email encryption should be a consideration for any organization that’s concerned about data confidentiality, privacy and integrity. As more and more communication continues to occur in digital form, understanding the benefits/disadvantages of the encryption options presented above is the first step in implementing the right solution.


